Kaspersky Software
Kaspersky Software

General requirements:
- 920 MB of free disk space
- CD/DVD drive (when installing from a CD)
- Internet connection (for installation and activation, participation in Kaspersky Secure Network, as well as database and program module updates)
- Computer mouse
- Microsoft Internet Explorer 8.0 or later
- Microsoft Windows Installer 3.0 or later
- Microsoft .Net Framework 4 or later
Netbook requirements:
- Intel Atom processor at 1.6 GHz or faster
- 1024 MB of free RAM
- Intel GMA950 video card with at least 64 MB of memory
- Screen resolution of at least 1024×600
Tablet requirements:
- Microsoft Windows 8, Microsoft Windows 8.1, Microsoft Windows 10
- Intel Celeron processor at 1.6 GHz or faster
- 1000 MB of free RAM
Supported browsers:
- Microsoft Internet Explorer 8.0 or later
- Mozilla Firefox 38.x and later
- Mozilla Firefox 43.x – 52.x
- Google Chrome 45.x – 55.x
- Mozilla Firefox ESR 38.5 – 45.2
Operating systems:
- Microsoft Windows XP Home Edition / Professional SP3 (32-bit) / Professional SP2 and later (64-bit)
- Intel Pentium 1 Ghz or faster (or a compatible equivalent)
- 512 MB available RAM
- Microsoft Windows Vista Home Basic / Home Premium / Business / Ultimate SP1 and later (32/64-bit)
- Microsoft Windows 7 Starter / Home Basic / Home Premium / Professional / Ultimate SP1 and later (32/64-bit)
- Microsoft Windows 8 / Pro / Enterprise (32/64-bit)
- Microsoft Windows 8.1 (Windows 8.1 Update) / Pro / Enterprise (32/64-bit)
- Microsoft Windows 10 Home / Pro / Enterprise TH1 / TH2 / RS1 / RS2 Preview (32/64-bit)
- Intel Pentium 1 Ghz or faster (or a compatible equivalent)
- 1 GB (32-bit) / 2 GB (64-bit) available RAM

Kaspersky Endpoint Security for Business
Next Generation endpoint protection
Protection as part of your business continuity strategy
Technology is a transformative force for business – keep pace or stagnate. But technology also opens the doors to criminals, and it’s the endpoint that is the prime target and source of the majority of problems. In the last year alone, over 38% of businesses suffered a cyber attack, while 39% of attacks aimed at protected endpoints succeeded. In this environment, companies need to be smarter than the cybercriminals attacking them.
Invest in the future
The average financial impact of a single data breach for small and medium businesses is $86.5k and for enterprises $992k. Next-generation anti-virus is no longer enough – only a multi-dimensional solution providing security at both multiple technological layers and functional layers of corporate IT infrastructure can deliver the protection you need. True endpoint security combines a variety of smart techniques and technologies to protect businesses against any kind of cyberthreat, on any platform. If you can protect your whole IT network, you ensure your business continuity.
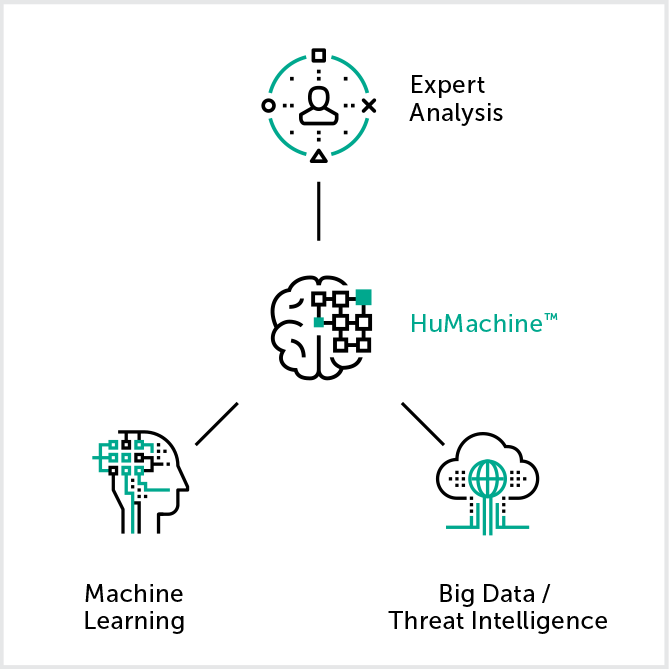
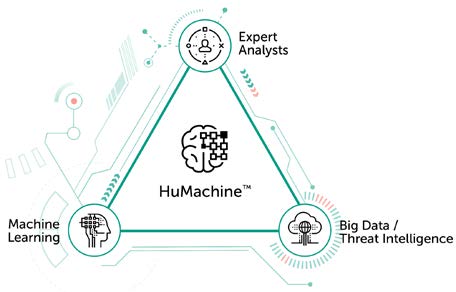
Protect what you value most with HuMachineTM-based applications
As your business matures, your IT security budget may not grow at the same rate. Resources must be optimized to meet the challenges of today – and tomorrow. Kaspersky Endpoint Security for Business, harnessing HuMachine™ intelligence, protects against ransomware, exploits and the most advanced cyber threats. Resource optimized, it’s packed with powerful security controls, automated vulnerability and patch management integrated encryption and can be controlled from a single console across the corporate network.
For as long as there are humans behind cyber attacks, there will be a need for human intellect teamed with innovative technologies to counter them. Kaspersky Lab’s protection is based on our global threat intelligence combined with machine learning algorithms, powered by the human expertise of the industry’s top specialists. We call this unique combination HuMachineTM, and it’s in our products’ DNA.
In 2017, Kaspersky Lab won the top award from Gartner Peer Insights for Endpoint Protection Platforms: the Platinum Customer Award. The award is the highest possible distinction in the competitive Endpoint Protection Platforms market. Our endpoint applications have achieved the highest percentage (90%) of top-three places in independent tests compared to any other vendor.
Agile, adaptive security
within any IT environment. It employs
a full stack of proven and Next
Generation technologies. Built-in
sensors and integration with Endpoint
Detection and Response (EDR) enable
the capture and analysis of large
volumes of data to ensure discovery
of the most obscure, sophisticated
cyberattacks.
Future-driven security for outsourced IT
threat prevention, mobile security,
data encryption and vulnerability
and patch management, empower
Managed Service Providers (MSPs) to
add IT security to their offerings.
Low footprint; high performance
HuMachine-based security delivers
optimum protection with minimal
impact on PC resources. Signatureless
components ensure threats
are detected even without frequent
updates.
Comprehensive protection
Kaspersky Endpoint Security for Business uses several Next Generation technologies (such as endpoint hardening, behavior analysis based on machine learning, exploit prevention, etc.) to neutralize the majority of threats before they hit the advanced protection layers. Suspicious files that make it as far as the endpoint is detected and blocked.ui.
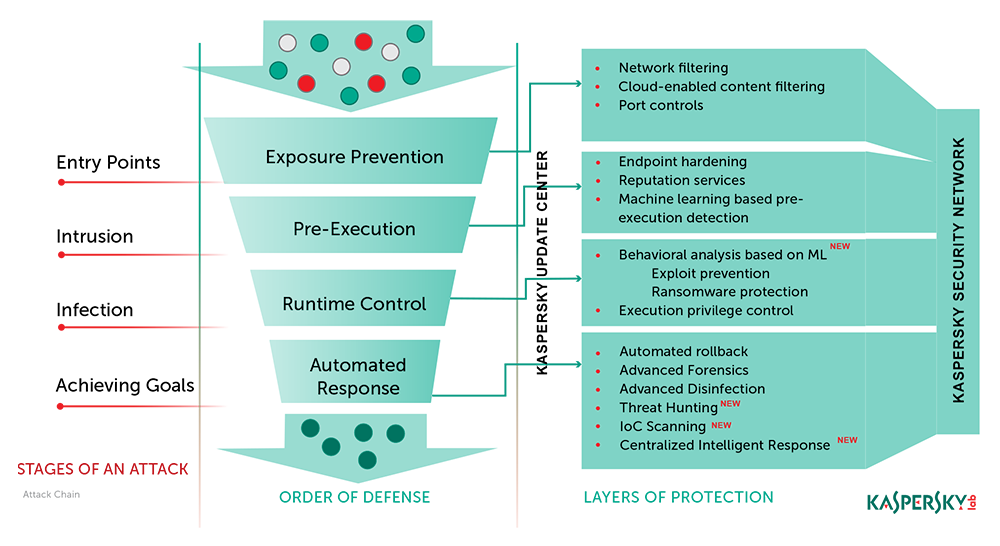
This combination of advanced technologies with our multi-layered approach achieves the perfect balance between performance and efficient protection. It plays a critical role in our products achieving one of the highest detection rates in the industry, as continuously demonstrated through independent tests.
Multiple protection layers for
• Android and other mobile devices
• Removable storage
• Windows and Linux Servers
• Mail servers
• Web gateways
• Collaboration servers
Unparalleled defense against
• Ransomware
• Mobile malware
• Unknown threats
• Fileless threats
• PowerShell and other script-based
attacks
• Web threats
• Email-distributed threats
• Phishing attacks
• Spam
Anti-Ransomware and Anti-Exploit protection
Based on unparalleled sources of real-time threat intelligence and machine learning, our technologies continually evolve. Protect your endpoints from the latest exploits and keep your data and shared folders safe and secure from advanced threats and ransomware.
Block account takeovers
Behavior Detection implements a Memory Protection mechanism, which guards system-critical processes and prevents leaking user and administrator credentials.
Lower your exposure to attack through applications
Detection and Exploit Prevention monitor the application’s behavior, block potentially malicious activity and protect legitimate applications from being exploited and used by malware. Your approved and trusted applications continue to run smoothly.
Neutralize rootkit
Attackers use rootkits and bootkits to hide their activities from security solutions. Anti-rootkit technology, part of Kaspersky Lab’s multi-layered, Next Generation protection, helps detect even the most deeply hidden infection and neutralizes it.
Spot more attacks and intrusions – even the most obscure
Built-in sensors and integration with Kaspersky Endpoint Detection and Response enable the capture and analysis of large volumes of data onshore without impacting on user productivity. It delivers advanced threat hunting for evidence of intrusion – such as indicators of compromise (IoC).
Prevent exposure via network
Malware using a buffer-overrun attack can modify a process already running in the memory and in this way execute the malicious code. The Network Threat Protection identifies network attacks and exploits and stops them in their tracks.C).
Beyond endpoint protection – now and in the future
Simplify inventory and patching
round-the-clock intelligence into exploited vulnerabilities, keeps potentially vulnerable software up to date saving your IT administrators time to spend on other tasks.
Secure data sharing through encryption
User-transparent FIPS 140-2 certified encryption fully secures confidential data on portable devices and on-site. Integrated technology means you can centrally enforce the encryption of corporate data at file, disk or device level and enable secure sharing of data across your network.
Support for remote and mobile scenarios
Data has become accessible anytime, traveling freely through the perimeter. Mobile security protects against threats specifically targeting data on the move, as well as attempts at using weaknesses in devices as springboards for subsequent infrastructure infiltration. Device Control guards against the consequences of data loss on unapproved or unencrypted portable devices and the uploading of infected
data from the device.
Optimize efficiency with management for all platforms
A single console gives you full visibility and control over every workstation, server and mobile device, wherever it’s located and whatever it’s doing. Almost infinitely scalable, the solution provides access to licensing, remote trouble-shooting and network controls. Centralized management is complemented
Regulate access to sensitive data and recording devices
Our solution restricts application privileges according to assigned trust levels, limiting access to resources like encrypted data. Working in step with local and cloud (KSN) reputations database, Host Intrusion Prevention System (HIPS) controls applications and restricts access to critical system resources, audio and video recording devices.
Stop Web threats before they reach your endpoints
By stopping the majority of incoming threats at the gateway level, we significantly reduce the impact of the human factor and workstation security specifics by not letting them reach the endpoints.
reduces the risk of vulnerability exploitation and considerably reduces operational overheads for IT security staff.
Increase productivity and reduce threats
Kaspersky Lab’s cloud-assisted, Next Generation anti-spam detects even the most sophisticated, unknown spam with minimal loss of valuable communication due to false positives. Reducing the time wasted, resources and risks associated with spam by stopping it in its tracks saves system and human resources. The protection incorporates multiple proactive security layers, including machine learning and
cloud-assisted threat intelligence, to filter out malicious attachments, known and previously unknown malware in incoming mail.
Enable secure collaboration
Our security for Microsoft SharePoint® includes anti-malware, content filtering and file filtering, to help your business enforce its collaboration policies and prevent inappropriate content from being stored on your corporate network.
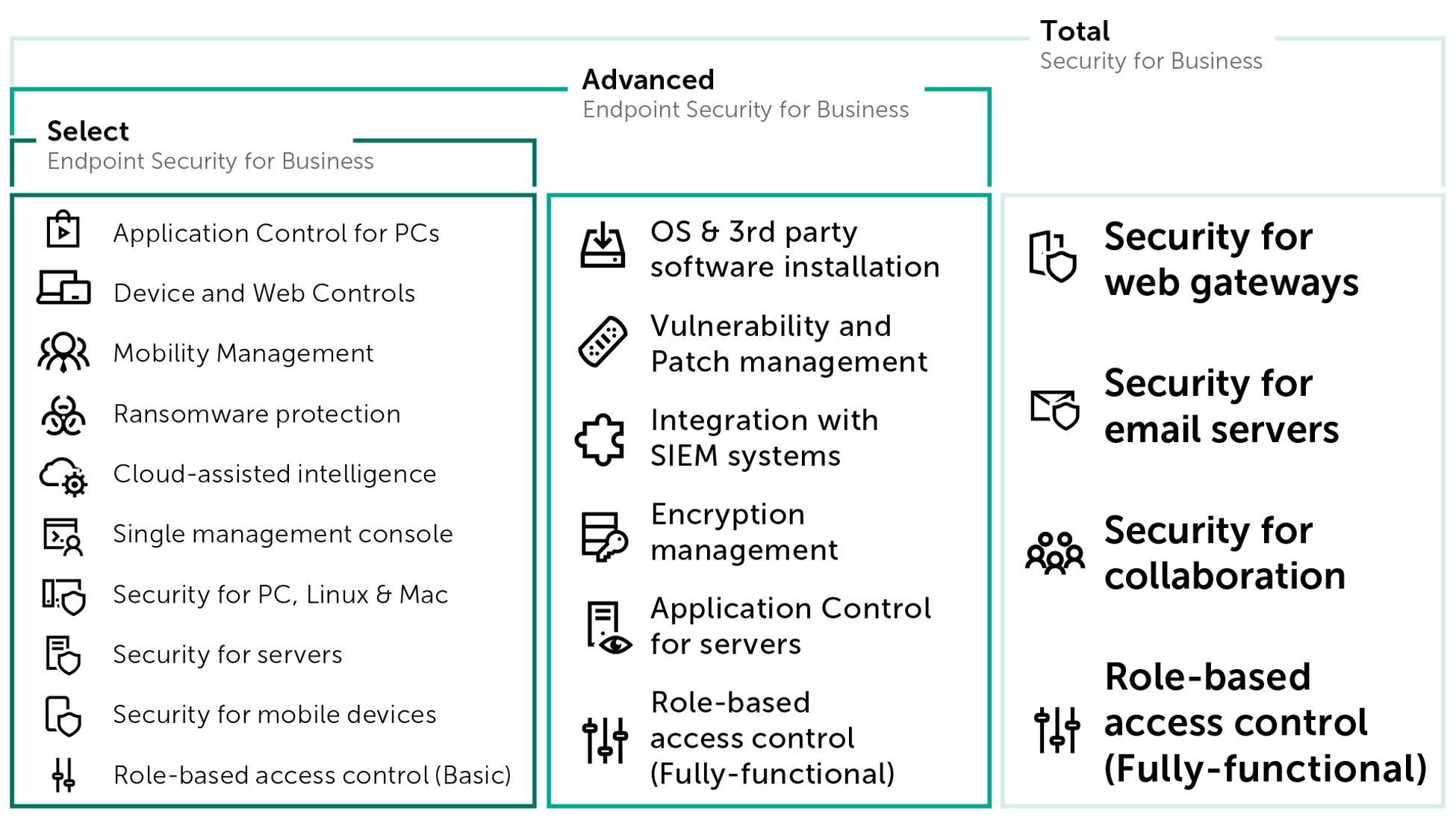
Kaspersky® Total Security for Business
Businesses that have mature IT environments – with a mix of recent and legacy systems – need to fine-tune their security for different systems. Our most comprehensive security solution for endpoints, infrastructure and collaboration servers lets you do just that – so you get rigorous security that you can tailor to your IT estate.
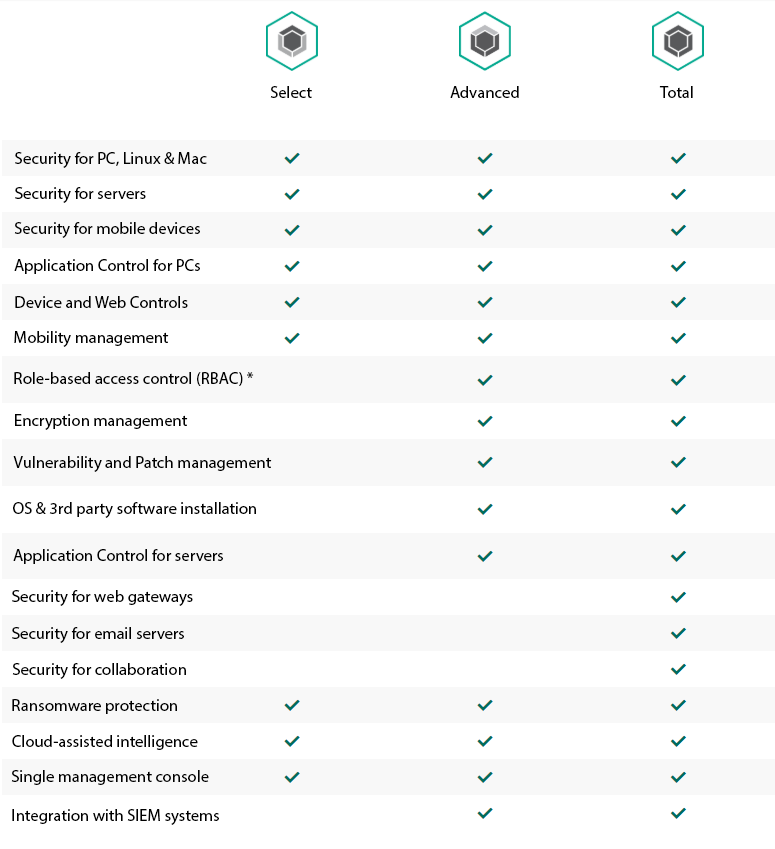
Kaspersky® Endpoint Security for Business Advanced
For security that works harder to protect your business, choose Kaspersky Endpoint Security for Business Advanced. As well as securing all your endpoints and servers, it delivers extra security layers to protect sensitive data and eliminate vulnerabilities – and it helps simplify systems management tasks too..
Kaspersky® Endpoint Security for Business Select
With more of your business operations going digital, you need to protect every server, laptop and mobile device. We deliver Next Generation security that helps you protect every endpoint your business runs, in a single solution with one flexible management console.
Which tier is right for you?
Adding more security as you need it
Also for Select customers, the Kaspersky Encryption Add-on enables Full Disk, File Level Encryption, utilizing strong encryption algorithms and featuring support for Single Sign-On for immediate access to encrypted files, as well as for smartcards / tokens for two-factor authentication. It lets you encrypt files and folders that are stored on local and removable drives.
For even more security without any additional complexity, just activate the required feature set from within Kaspersky Security Center.
Why upgrade your current endpoint protection?
technologies – quick
and easy: one server, one
console, single agent
process via deeper
integration – single code
base, built in-house
separate licensing – all
the functionality you need
in a single purchase
control capability; unified
management with rolebased
access
• Active hunting for threats as a result of the integration between endpoint protection and Endpoint Detection & Response or Anti Targeted Attack solutions.
• Unique cloud mode for protecting components delivers optimum protection with minimal impact on PC resources and Internet bandwidth usage.
• Support for Microsoft Windows Server containers, external traffic security and firewall management.
• Enhanced Device Control and Anti-Bridging functionality.
• Enhanced Application Control with Trusted Certificates category and Test Mode for policies.
• The new clean user interface visualizes the multi-layered protection, showing the status of protection and the effectiveness of Kaspersky Lab’s latest technologies in action.
True Cybersecurity: It’s In Our DNA
• Our expertise is from the top down – starting with our CEO, Eugene Kaspersky.
• Our Global Research & Analysis Team (GReAT) – elite group of security experts has discovered many of the world’s most dangerous malware threats and targeted attacks.
• Our groundbreaking Global Transparency Initiative is further evidence of our commitment to protecting customers from cyberthreats, regardless of their origin or purpose.
Build up your GDPR compliance with True Cybersecurity
Kaspersky Lab raises awareness about the cybersecurity-related aspects of GDPR. Our solutions help customers reduce the risks of a data breach and prevent security incidents. We also help our customers’ DPOs with enhanced visibility of the monitored infrastructure.
The Bigger Picture – Kaspersky IT Security Solutions for Business
Endpoint protection, though critical, is just the beginning. Whether you operate a best-of-breed or single-source security strategy, Kaspersky Lab offers a range of products that interlock or work independently, so you can pick and choose without sacrificing performance efficiency or freedom of choice.